Information Security Risk Management Framework
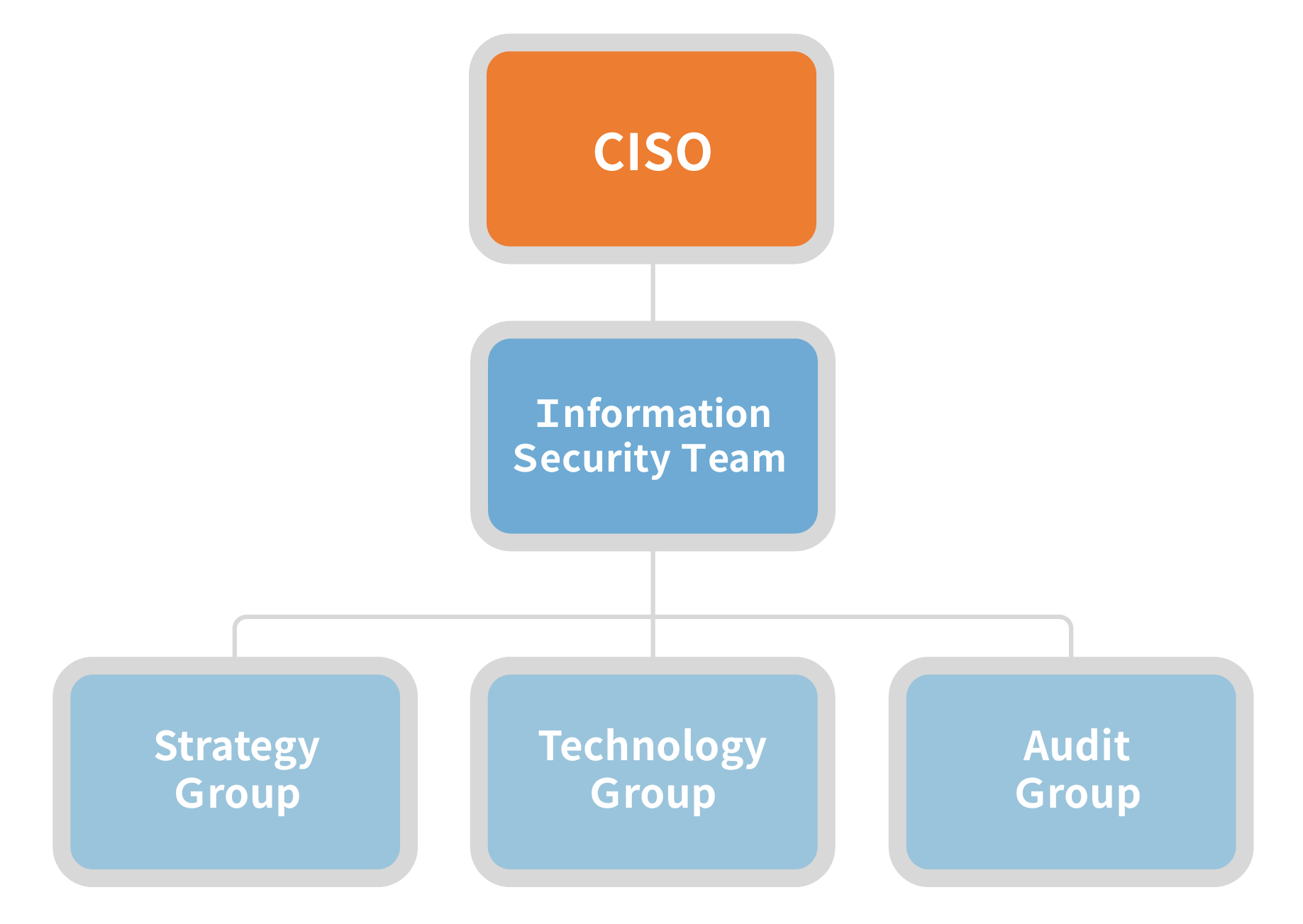
The Company appoints a Chief Information Security Officer (CISO) to oversee information security affairs. An information security team has been established with three groups: Strategy, Technology, and Audit. The team plans, executes, analyzes, and coordinates all information security matters, regularly reporting implementation status to management.
Information Security Policy
- The Strategy Group plans and promotes information security policies, management practices, and introduction programs for products or services.
- The Technology Group implements management practices and supports product/service proof-of-concepts (POCs), deployment, and ongoing maintenance.
- The Audit Group assists the internal independent audit unit with yearly reviews of information security policies and procedures to ensure effective execution, and proposes improvement plans with tracking.
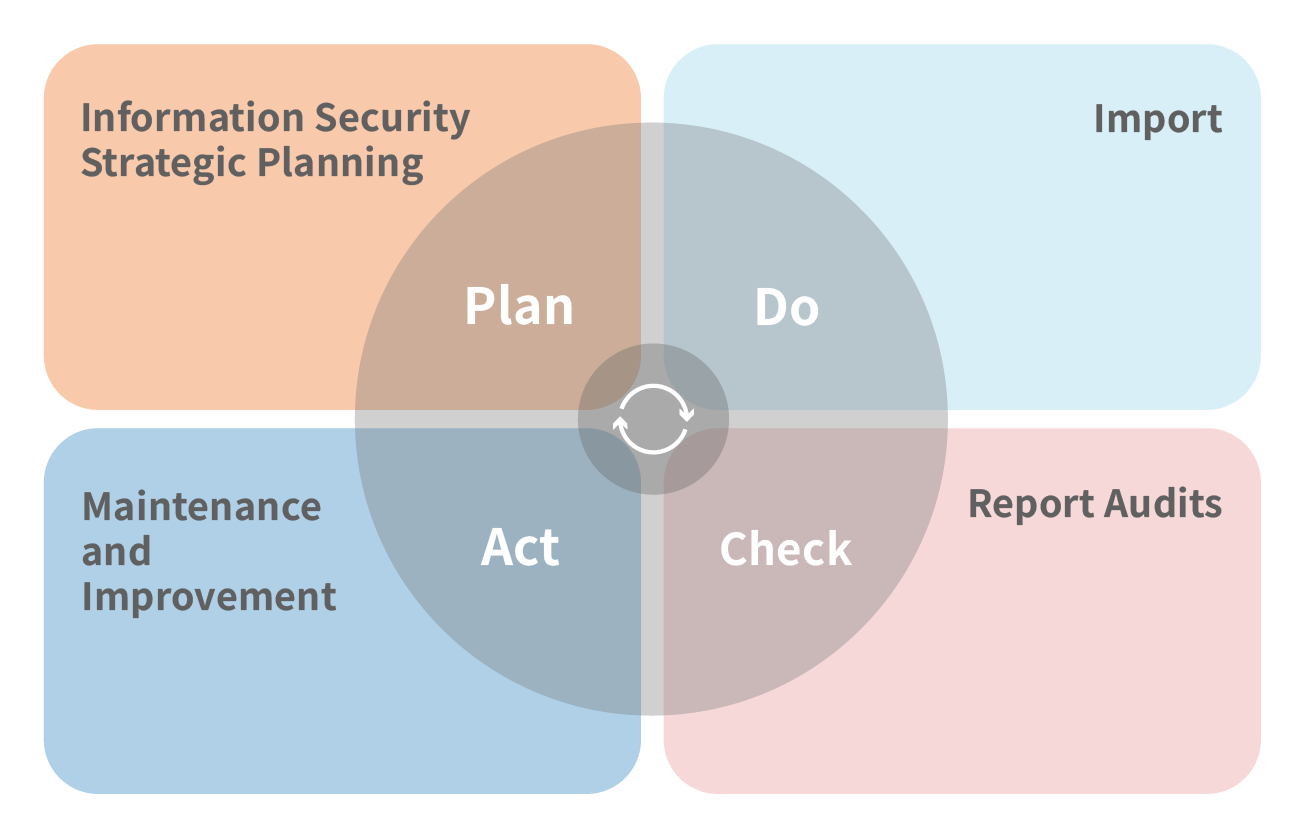
- The team jointly confirms maintenance and improvements, continuously driving the PDCA cycle.
Information Security Policy
Specific Plans and Resources Invested in Information Security Management
- Antivirus endpoint protection deployed on personal computers and servers.
- Internet firewall with application identification and advanced threat protection to strengthen defense against external attacks.
- Internal firewall with whitelisting of authorized services to reduce risk exposure.
- Identity modules to differentiate between employees and visitors and segregate access paths.
- Advanced threat protection modules added to spam filters to prevent phishing attacks on sensitive data.
- Active alert systems to automatically notify of threats and configuration changes.
- The Company has contracted professional vendors to provide SOC/MDR services, enabling 24/7 continuous monitoring and analysis of cybersecurity threats.
- Vulnerability scanning systems continuously identify system vulnerabilities, with ongoing tracking and remediation to reduce security risks.
- Multi-factor authentication (MFA) to reduce account credential theft risk.
- Continuous social engineering exercises and training to boost employee security awareness.
- Ongoing professional training for information security personnel to ensure compliance with standards.
- Participation in cybersecurity joint defense organizations like TWCERT/CC to strengthen the joint defense system and threat intelligence sharing.
- The Company has obtained ISO/IEC 27001:2022 and CNS 27001:2023 certifications, valid until December 12, 2028.
<Certificate Download>
Information Security Management Plan
Although the Group has established comprehensive cyber and computer security defenses, it cannot completely guarantee that critical enterprise systems will be fully protected against all external intrusion attempts. In the event of a serious breach, systems might become inoperative, potentially disrupting operations or delaying shipments and causing customer losses. Swift recovery of system operation is therefore a top priority.
To support this, the Company continues to invest in security equipment and software, and strengthens redundancy through the following measures:
- Local data snapshot backups to rapidly restore data if hardware remains intact.
- Asynchronous replication to an off-site center (over 30 km away) for dual data protection.
- Weekly off-site storage of full backup data.
- Periodic drills to switch primary data center operations to the off-site location when needed.
These steps aim to restore company operations in the shortest possible time after an incident. For further details on security and future planning, please refer to WT Sustainability ESG website.
ESG-Information Security
